IT Consulting & StrategySecurityTech Support & Managed IT ServicesConstructionEducationFinanceHealthcareLegalReal Estate
It’s not unusual for people to assume that keeping their network safe is as simple as throwing up a firewall and using some anti-virus software.
That might have been true in the early days of computers and the internet, but, really, the single-solution-security-system only ever really applied to personal computers.
Keeping businesses safe from data breaches and cyberattacks is a lot more complex these days. There isn’t just one layer of security between you and a potential threat; there are seven – each with specific security needs to help keep your businesses safe.
What are they, and how can you make sure they’re secure? Read on…

The OSI model
In the late 1970s, the International Standards Organization (ISO) realized there needed to be standards in how computers networked given the different makes, models, technologies, etc. They developed the Open Systems Interconnection (OSI) model with its seven layers of cybersecurity as a reference to show the various layers on a network and how everything was interconnected.
The OSI model’s seven layers are the: Human Layer, Perimeter Layer, Network Layer, Endpoint Layer, Application Layer, Data Layer, and Mission Critical Layer. Each layer represents a different stage in network communication, from someone typing on a keyboard to the data your system uses for applications.
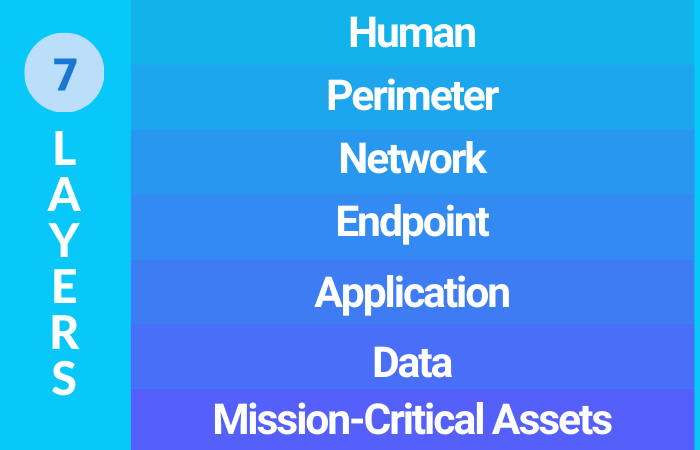
This model was eventually replaced by the TCP/IP model, which serves as the basis for the modern-day internet. But the OSI model is still helpful in getting people to visualize how their data moves through a network and where to implement security measures.
The Seven Layers of IT security
When you look at the OSI model, it’s pretty clear you need more than just a few security protocols in place to be fully protected. You need to carefully consider all the potential access points and areas where hackers may gain entry to your network, data, and business.
Let’s take a closer look at the 7 layers, how they’re vulnerable, and what you can do to protect them.
Human Layer
People are, hands down, the weakest link in almost every way possible when it comes to cybersecurity. In fact, according to reports, upwards of 90% of all security breaches are caused by humans. It’s not so much that people are deliberately letting hackers into their systems; we just happen to be the one area that is most easily exploited. We get distracted by our jobs (and our daily lives), and we don’t always fully understand the technology we’re using or how to keep it safe.
The best approach to keeping the human layer secure is education and training. Getting an education program set up to train employees on the benefits of good cybersecurity habits regularly can significantly reduce the likelihood of a successful attack. This includes instruction on how to spot a phishing attempt, good password habits, and information on current scams to be on the lookout for.
Access controls are also a good idea for securing the human layer since they can limit the amount of damage in case there is a successful attack.
Perimeter Layer
This is the outer layer of your network. It’s the point where everything connects and gains access to your data. It includes wireless access points (for example), but it also includes any and all devices connected to your network.
It wasn’t that long ago that the perimeter was fairly easy to secure. The devices that connected to your network were limited to computers. Now, however, you have to consider everything. Desktop computers, laptop computers, printers, copy machines, cell phones, even lightbulbs if you’re a company that uses Internet of Things (IoT) devices.
At this level, the first step is figuring out what your perimeter actually looks like. This means cataloging all the devices connected to your network, something that’s especially challenging with the big work from home push we saw in 2020. To keep this layer safe, you have to know what it looks like.
Next, figure out what data is passing through this layer. The chances are that’s going to be all your important business data.
Finally, secure everything – data and devices. This means things like firewalls, encryption for your data, anti-virus software, device management (especially important if you have a bring your own device policy), and creating a secure demilitarized zone for an extra layer of protection.
Network Layer
Similar to the perimeter layer, the concern here is who and what devices can access your system. But, the bigger part of the network layer is what people and devices can access once they’re inside your system.
The best practice for security at this layer is to give employees and devices access to the parts of the network that are 100% necessary to do their jobs. The main reason for this is that if something happens, the damage is contained. If no one person has access to everything, then any successful cyberattack only results in a small part of the network being breached.
This ensures you can limit any damage caused by human error, as well as the impact of any devices that may be compromised.
Endpoint Layer
An endpoint is any device that is connected to your network, and, as we touched on above, the sheer number of these devices on networks these days can be a little overwhelming. That’s why it’s important to have a good policy in place to monitor and manage these devices.
Encryption is key at this level, but it can’t just be limited to your data. You need endpoint encryption in place to ensure that the devices themselves are running in secure environments. Mobile device management (MDM) is also a critical aspect of endpoint security. MDM allows you to restrict access to certain devices on your network, which is great, but it also gives you remote access to devices. This feature lets you lock down mobile devices and delete all their data to prevent further damage.
Application Layer
The application layer revolves around the software you use in your business. Microsoft Office, Slack, Zoom, and everything else that you use to help keep things moving at work all need to be secure.
The easiest thing you can do here is to make sure your apps are always up to date. This helps ensure that any known security problems are fixed and that the application is as secure as possible. Beyond that, next-generation firewalls that come with integrated app protection will help keep things safe, as will using sandboxes for browser-based applications and using tight software restriction policies to prevent unauthorized software from being run on your network.
Data Layer
In almost every instance, data is the target when it comes to cybercrime. This is the layer that requires the most attention because it’s the heart and soul of your business.
The kind of data that you have is going to depend on your business, but it could include customer data, payment information, social security numbers, business secrets (and other intellectual property), and healthcare information. Losing this data erodes your customers’ trust in your business, leaves you open to huge regulatory fines, and about 50% of the time, causes your business to close.
Keeping things safe at this level involves file and disk encryption, regular backups of all critical data and processes, two-factor authentication, enterprise rights management, and policies that ensure data is wiped from devices that are no longer being used or that are being sent to another employee for use.
Mission Critical Assets
This is anything your business can’t survive without. This includes operating systems, electronic health records, software tools, financial records, and cloud infrastructure.
The challenge at this layer is that what’s mission-critical for one business isn’t necessarily critical for yours. That means you have to determine what your business can’t live without and work backward to protect it.
What’s really nice about this method is that it allows you to customize what you do at each of the six layers that come before the mission-critical assets. While each layer of security focuses on a different aspect, the overall goal for all seven layers is to keep your business running and secure at all times.

Get 7 layers of protection
Keeping track of and monitoring the seven layers of security can be a challenge. Even if you have a dedicated IT team, there are a lot of pieces that need to be watched, and it’s easy for something to get missed.
That’s why having a team of experts can provide your business with the level of security you need to protect your seven layers. That’s where we come in. Through Kaytuso, our managed security services provider, we can take care of all of it, from educating employees to making sure your mission-critical assets are fully protected.
Ready for comprehensive security coverage that keeps your business running? Contact us today.
[sales-phone] | [email-address]



 January 21, 2021
January 21, 2021 Homefield IT
Homefield IT

