IT Consulting & StrategySecurityConstructionEducationFinanceHealthcareLegalReal Estate
The National Institute of Standards and Technology (NIST) is a government agency that promotes innovation by providing metrics and standards for the science and technology industry. While the agency has produced many standards over its 100-year history, the most commonly discussed in the IT industry is the NIST Cybersecurity Framework – a system of controls and guidelines that are being adopted by a growing number of businesses in order to strengthen their cybersecurity protections.
While in the past NIST was mainly used by larger organizations who had the resources to pursue strong cybersecurity, that’s now changing. In August of 2018, the Federal Government signed the Small Business Cybersecurity Act – a revision of the NIST framework that provides small and midsized companies with a consistent set of guidelines and resources they can use to protect themselves against cyberattack.
A New Era for NIST and SMBs
The law, which passed with strong bipartisan support, was drafted in response to the growing cybersecurity threat that SMBs are facing. Hackers see SMBs as the “low hanging fruit” on the security pecking order. These businesses, while relatively unprotected, still possess a great deal of valuable data that hackers can hold for ransom, or sell on the dark web.
While the expanded NIST framework isn’t a mandatory regulation, and won’t do much to deter cybercrime by itself, it does help SMBs counter cyber threats by making resources and best practices more easily accessible.
For example, in the past, experts had criticized the NIST framework for being too costly to implement, even at large business. To solve this, the updated framework has been designed to work with commonly used off-the-shelf products and technologies, so that businesses of all sizes can improve their security in a reasonable timeframe while also controlling costs.
The Key Components of the NIST Cybersecurity Framework
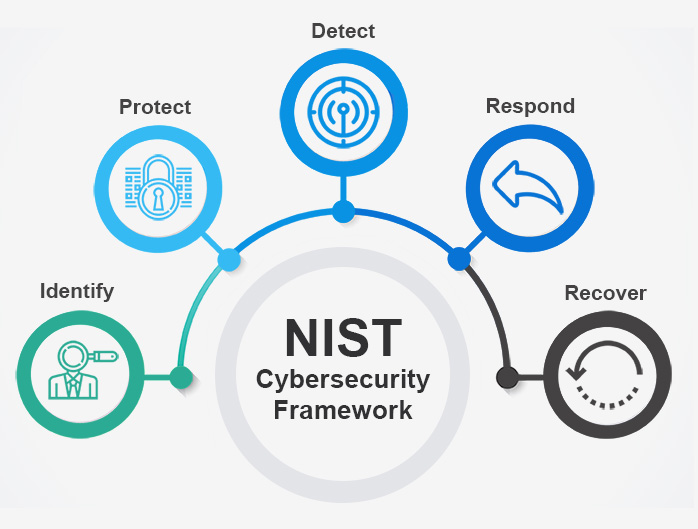
The NIST framework is organized around five high-level core functions, Identify, Protect, Detect, Respond, and Recover. These core functions can be thought of as organizing principles that give shape to the framework’s implementation. Here’s what each of them means.
Identify – Gain full visibility of your physical and digital assets, and their vulnerabilities
Protect – Control access to those assets with appropriate safeguards
Detect – Possess visibility over your network and identify threats quickly
Respond – Contain cybersecurity events with a response plan and clear lines of communication
Recover – Effectively recover any damaged services with clear action points
Another useful feature of the NIST framework is the tiered stages of implementation. These tiers provide businesses with a clear guideline to understand their progress and a means of improving internal communication. They’re designed to be pursued in ascending order.
- Tier 1 – Begin to cultivate a cybersecurity consciousness across your organization
- Tier 2 – Implement NIST frameworks and risk management policies
- Tier 3 – Maintenance of cybersecurity policies and controls
- Tier 4 – Advanced staff training and implementation of cybersecurity tools.
Want more information about what each of these tiers involves? You can view the NIST cybersecurity roadmap, located here.
Steps to NIST Implementation
While there are general guidelines for the implementation of the NIST cybersecurity framework, the process is very flexible, especially since the advent of the small business cybersecurity act. None of the steps in the framework are a one-sized fits all approach. Instead, take the time to customize each step to the needs of your business.
Step 1 – Evaluate and Set Goals
The earliest stages of NIST cybersecurity framework implementation involve setting organizational goals. The reason it’s important to start by setting goals is that many businesses have difficulty agreeing internally on an acceptable level of risk. Clarifying those needs across your organization first, by getting IT and other departments on the same page will help ensure the NIST framework is implemented efficiently and effectively.
Step 2 – Develop Profiles
Besides the two concepts mention above, another important part of the NIST cybersecurity framework is the notion of a profile. There are two common types of profiles. The Current Profile, which is where your organization currently stands with regards to the NIST guidelines, and the Target Profile, which represents your desired level of cybersecurity readiness after the framework is successfully implemented.
Once you’ve clarified your goals, you can begin developing a Current Profile. This process should include a thorough risk assessment of your company’s IT systems, while simultaneously referencing the five main categories and the 23 subcategories of the NIST Framework to locate areas of weakness. Here are some topics that this will likely include:
- Determining what valuable data your company is storing and the exact value of that information
- Mapping which components and sub-systems of your network interact with that valuable data
- Analyzing the potential risks to those systems and gaps in your current cyber defenses
Step 3 – Execute a Plan of Action
With a clear sense of where your company currently stands, where you’d like to end up, and the issues that are separating you from your goal, it is time to begin taking steps to close those gaps. As with the early planning stages, make sure that the work of NIST framework implementation is done by an educated staff who understand its importance, and are given clear responsibilities at each stage.
Step 4 – Maintenance
As with any cybersecurity project, it is important to look at NIST adoption not as a one-time event, but as an ongoing program that needs maintenance to provide maximum benefit. Do you have an internal team dedicated to cybersecurity? If not, it may be time to either form one or enlist the help of an external security partner who can perform regular audits and ensure that your protections reflect changes in your network and organization.
NYC’s NIST Expert for Small and Midsized Businesses
We understand that not every small or midsized business is going to have the internal resources to make sure that the NIST cybersecurity framework gets properly implemented every time. If you’d like help implementing NIST, or with any other aspect of your cybersecurity strategy, then we urge you to contact the experts at Manhattan Tech Support. For over 20 years, we’ve been helping businesses in NYC strengthen their cybersecurity protections with global best practices, including the NIST cybersecurity framework.
Have a cybersecurity question? Get in touch anytime at [sales-phone]!
SEE MORE
Kaytuso – the cybersecurity & regulatory compliance division of ManhattanTechSupport.com LLC.
Exceed Digital – the custom software development and business intelligence solutions division of ManhattanTechSupport.com LLC



 April 5, 2019
April 5, 2019 Homefield IT
Homefield IT