IT Consulting & StrategySecurityTech Support & Managed IT ServicesConstructionEducationFinanceHealthcareLegalReal Estate
What is National Cybersecurity Awareness Month?
For the last 17 years, October has been National Cybersecurity Awareness Month (NSCAM). It started back in 2004 as a joint effort between government bodies, the U.S. Department of Homeland Security and the National Cyber Security Alliance (NCSA), and industry partners to help spread awareness about the risks of being online.
The goal was to help Americans stay safer and more secure online. The internet had been a part of the mainstream for about a decade by this point, and there was a need to educate people about the potential risks and how to mitigate them. At the time, efforts focused on creating good cybersecurity habits, like updating your antivirus software twice a year.
As the program grew, it became more focused on the message it put out each year, and on how NSCAM was helping people stay safe. Themes were introduced as a way of helping create targeted campaigns, industry participation grew, downloadable toolkits were introduced, and the government took a more involved role in help spreading the message.
2010 saw the introduction of the STOP. THINK. CONNECT. campaign. This was a global effort to spread a message that encouraged safe online habits and to promote the idea that online security needs to be second nature for people everywhere. The goals of STOP. THINK. CONNECT. are:
- Increase awareness of cybersecurity, while reinforcing its importance.
- Communicate strategies the public could use to keep themselves safe online.
- Shift the conversation from avoiding danger to acknowledging that cybersecurity is a shared global responsibility.
- Increase the number of stakeholders engaged in creating and promoting cybersecurity awareness.
NSCAM used a few different approaches to push the goal of engagement. The first was the use of themes to help them create specific guides for the month. Between 2009 and 2018, as an example, the theme was “Our Shared Responsibility” and in 2019 and 2020, the themes were “Own IT. Secure IT. Protect IT.” and “Do Your Part. #BeCyberSmart.” respectively.
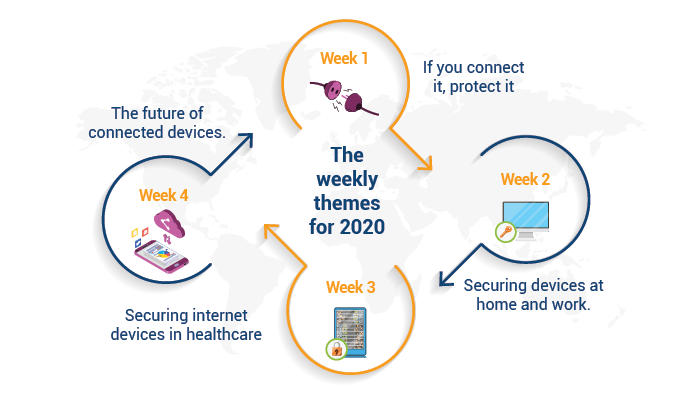
This was further broken down into themes for each week. These weekly themes allowed NSCAM to provide specific talking points and activities to help push awareness of what the threat landscape looks like for a given year. The weekly themes for 2020 were:
- Week 1 – If you connect it, protect it.
- Week 2 – Securing devices at home and work.
- Week 3 – Securing internet devices in healthcare.
- Week 4 – The future of connected devices.
For more details on how each week’s theme, please check out this infographic – Image courtesy of Center for Internet Security®
As you can see by the themes, their focus this year was on the increase in connected devices in our lives, which is everything from our phones to lightbulbs, printers to doorbells, and what we can do to prevent attacks.
To help really push engagement, NSCAM created their Champions program. Under this program, businesses, non-profits, schools, and individuals (among others) could register online to download a toolkit that helped them implement their own NSCAM programs.
In 2019:
- 2,477 organizations and individuals registered as Champions, an increase of 23% over the year before.
- 17,118 toolkits were downloaded.
- The combined reach of all the Champions was 50.4 million people, in all 50 states and 40 countries worldwide.
The state of cybersecurity today
One of the reasons NSCAM is still going strong is the ever-increasing risk of cyberattacks. It’s not just that we need to worry about our computers getting infected with a virus. Cyberattacks now have the potential to affect every aspect of our lives.
The proliferation of connected devices in our everyday lives means we must be more careful. Attacks can target our phones, tablets, and computers. Plus, the increase in the number of devices on the Internet of Things, or smart devices like lightbulbs, autonomous cars, doorbells, and thermostats, means that there are more possible attack vectors than ever before.
There’s a huge risk for people personally and an even greater risk for companies.
Overall, there is a hacking attempt made every 39 seconds. That’s 2,244 attempts each day. They’re not all successful, but that’s enough to create a need for the increased spending on cybersecurity that we’ve been seeing, to the tune of $123 billion in 2020 according to Forbes.
With all that spending, it’s easy to think that attacks are being curbed, but that’s not the case. In the first half of 2019, 4.1 billion records were exposed as a result of data breaches – the grand total in 2019 was 7.0 billion records exposed as a result of 5,183 breaches. This was a 33% increase over the previous year.
Of the breaches that occur every year, 86% are financially motivated, meaning they were ransomware attacks or other forms of attack that are engineered to get money from the victims.
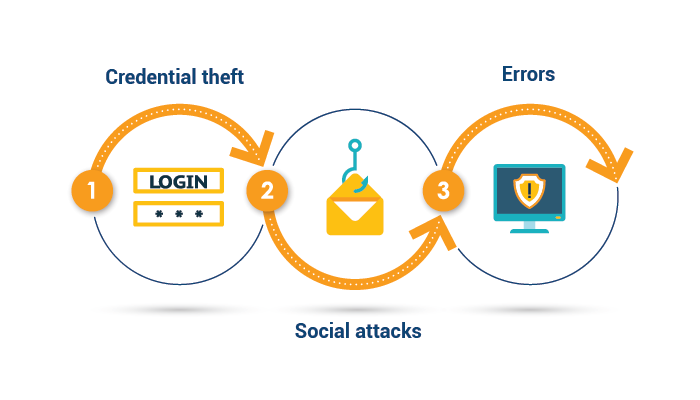
67% of all breaches were caused by three types of attacks. They are:
- Credential theft – Hackers obtain log-in data and passwords to gain access to a system.
- Social attacks – Phishing or other trickery where hackers dupe everyday users into providing access.
- Errors – Hackers exploit errors in the system (which are often caused by humans) to gain access.
What makes these breaches particularly damaging is that it takes 206 days to detect them. That’s nearly seven months where compromised data has been missing without people noticing. To add to that, the average cost of a data breach is currently sitting around $3.92 million, between lost business, regulatory fines, and the cost to repair the problem. The final blow here is that almost half of all attacks are focused on small-to-medium-sized businesses and it should come as no surprise that most businesses, 60% in total, go out of business after suffering a breach. The cost to recover is just too great.
Of course, everything changed with COVID-19 and the massive shift to a work from home setup for many employees around the world.

The state of cybersecurity in COVID-19 times
By the end of March 2020, most of the world took notice of the spread of COVID-19, and, in an effort to slow down the virus, there was a huge shift to work from home (WFH) for anyone who could do it.
Prior to the start of the pandemic, only around 7% of the workforce in the US even had the option for WFH at their job. For the most part, WFH was limited to executives or jobs like IT managers. Once the global pandemic was declared, 88% of global organizations either required or encouraged their employees to work from home.
This was great for social distancing, but from a cybersecurity perspective, things took an almost immediate turn for the worst.
With the sudden shift to WFH came a huge uptick in cyberattacks. It wasn’t so much that cybercriminals had more time on their hands, as it was that there was a huge influx of technology being used for business when it shouldn’t have been. The number of unsecured desktops being used for business jumped by more than 40%. This, in turn, led to a 400% increase in brute force attacks on remote machines and a staggering 667% increase in email scams related to COVID-19. What really drives home the impact of these attacks is that users are three times more likely to click on COVID-19-related email attacks.
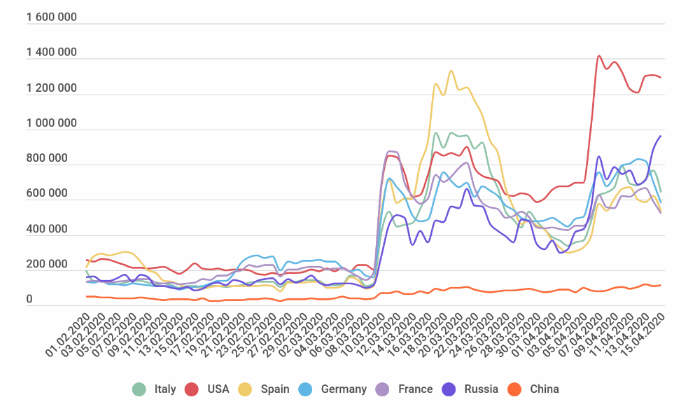
The spike in brute force attacks occurred in March when the workforce started working from home. Source: Kaspersky
Along with an increasing number of known attack vectors, there was a whole slew of new ones. Perhaps the most well-known is Zoom. The video conferencing platform had been popular among WFH folks for a while now, but when COVID hit, the whole world jumped into a Zoom room. This resulted in over 500,000 Zoom credentials being hacked and sold on the Dark Web. And a 2000% increase in malicious files that contained the word Zoom (these files could be used to gain access to systems remotely). It also led to the discovery of exploits in Zoom that allowed anyone at all the jump into a room, regardless of whether or not they were supposed to be there, resulting in the Zoombombing craze that plagued the first few months of the pandemic. Zoom has since patched a lot of these vulnerabilities and tightened the default settings to minimize the impact of these threats.
It hit the point early on where it became hard to look for information about COVID-19 without running into a site that was compromised, as tens of thousands of scam sites related to the pandemic popped up almost immediately.
Attention Small Business Owners: Why You Should Care
Cyberattacks affect almost every aspect of your business. It’s not just that you lose money due to downtime or get fined by regulatory bodies and it’s not just that cybercrime is targeted at large corporations. Small businesses account for roughly 50% of all attacks. And, beyond the financial impact of a cyberattack, your reputation takes a huge hit.
When you suffer an attack, customers become aware of the fact that you haven’t taken their data seriously. To them, you’ve made a choice not to prioritize security and, as a result, their information was compromised. The result is that they’re going to find another business. Larger companies aren’t going to feel the impact of customers leaving the same way an SMB does.
Not only do customers lose trust, but partners and vendors do, as well. Any business information that they’ve shared with is potentially at risk during a breach. The worst-case scenario here is that you end up being the entry point to a vendor you use.
Cybercrime stats for SMBs
- Cybercrime costs an average of $200,000 for SMBs.
- Downtime costs SMBs $137 to $427 per minute.
- 23% of small businesses don’t use endpoint security.
- 28% of data breaches in 2020 were small businesses.
- 84% of SMBs are targeted by phishing attacks.
Cybercrime stats for enterprises
- Cybercrime costs enterprises an average of $8.19 million.
- Downtime costs $5,600 per minute to nearly $9,000 per minute.
- 15% of enterprises businesses don’t use endpoint security.
- Enterprise businesses accounted for 72% of data breaches in 2020.
- Phishing accounts for as many as 93% of security breaches.

What you can do to stay safe online
Even before the pandemic, there was an increased need to be smart about how you used the internet. But, since the pandemic brought on a significant increase in cyberattacks, the need to improve our knowledge of cybersecurity measures has been apparent, especially if working from home becomes a regular part of life after.
We’ve put together some tips to help you promote good online habits within your company. These tips are useful for personal use and at work.
Establish clear security best practices
It starts with having good protocols in place. The more explicit you are about your security practices, the more like you are to reduce the chances of a breach. This includes things like password management practices, character length, and how frequently they get changed. You can encourage self-reporting when people make mistakes, like clicking on a link they shouldn’t have. And having an incident response plan.
Most of what we’ll be mentioning in this list can help you set up these kinds of protocols you need to help keep your business and employees safe online.
Education and training
The single biggest thing you can do to be safe online is to put a focus on education and training. Take a look at the most common ways criminals can access your system:
- Weak and stolen log-in credentials
- Insider threats
- Improper configuration and user error
- Malware
- Social engineering, like phishing attacks
- Back doors and application vulnerabilities
- People having access to information they don’t need, access control
Of the seven listed, five of those can be directly tied to people. Humans continue to be the single biggest point of weakness when it comes to cybersecurity.
The more time you spend educating your employees about cybersecurity, the better. Focus on creating awareness around phishing. As mentioned, there has been an explosion in phishing attacks this year and an increase in the likelihood that people will fall for it. The more time you can spend not only educating your staff about what a phishing email looks like and things to watch for, but also talking about what current scams are going around, the better. One of the things that have come up as a result of people working from home is the increased levels of distraction that are caused by home life. This means that people are potentially not paying as much attention to emails as they come in and are clicking on things that they might normally avoid.
Also, cover topics like good password protocol, including character length and how frequently they should be changed. If you can create a policy around this, even better. If you need to, allow employees to use a password manager to help people maintain good practices.
If you can, try to schedule regular meetings to provide updates to your team.
Limit access to critical systems
To take the idea of people being the weak point one step further, ensure that people in your organization only have immediate access to the parts of your system that are necessary to do their jobs.
When employees have access to your entire system, it can become a major entry point for criminals. They can gain access to everything using methods like phishing and, if they target a low-level employee who has more permissions than they need, your entire business can be compromised.
Using a setup like role-based access control (RBAC) can prevent this. RBAC is exactly what the name implies, employees can only access the parts of their system that they need to for their job. It creates an immediate limit to what hackers can access should that user be compromised.
You can also implement network segmentation, which creates a series of smaller subnetworks from the main network. This, again, limits what criminals can do if they breach your system, as the subnetwork is a closed system that doesn’t allow access to the network as a whole.
Finally, remember to limit access to physical systems as well. As Google learned the hard way a few years ago, physical access points matter. If you can’t control access to your physical servers, you’re leaving the door open to attacks, especially during the pandemic when most people are more likely to be out of the office.
Perform regular updates
One of the ways cybercriminals can gain access to your system is by exploiting flaws in outdated systems. Zoombombing is a great example of this. There was a flaw in Zoom that allowed people to crash meetings. In this instance, it was mostly just a way to be mischievous, but that’s not always the case.
Software companies are always updating their apps these days to ensure that these exploits are patched as quickly as they’re found. Making sure that you are using the most recent version ensures that you’re not leaving backdoors to your system open.
This is especially important this year as there has been a huge increase in cyberattacks that target web applications. These attacks now account for 43% of breaches, which is nearly double what it was last year.
When updating, make sure to include:
- Any and all applications you use in your business.
- Hardware and firmware.
- Operating systems.
- Virus and malware definitions.
Make regular backups
If something does go wrong, backups can be the thing that separates a minor problem from a huge issue.
One of the things that has a major impact on businesses is downtime. The longer it takes a business to resolve an issue and get online, the more money that is lost, the cost can be upwards of $9,000/minute.
Backups help you reduce that time because if something happens, you can restore the system to the way it was before the attack. The trick, though, is maintaining a regular backup schedule. A backup is effectively useless if you’re reverting to something that was capture six months before the attack.

Keeping WFH employees safe online
In the current working climate, you have to take extra steps to ensure that your workforce is staying safe online. It’s one thing when everyone is working in the office on a secure network, with approved computers that limit what software can be installed. But in a WFH home setting, everything changes.
Suddenly, employees are using unsecured home networks and are most likely still using default passwords on their modems. They’re sharing the space with families or roommates. They may even be using home computers that don’t have any kind of access restriction protocol in place, so they can install or modify any program they want.
Here are some things you can do to prevent this from becoming a cybersecurity nightmare.
Use VPNs
The absolute bare minimum when it comes to cybersecurity when working remotely is using a virtual private network or VPN. A VPN is a continuation of your secure business network that allows employees to remotely access your system through a secure channel. It’s pretty much a safety tube for your business data.
When users log in to a VPN to gain access to your network, they’re working through a system that is encrypted, prevents others from learning your location, and hides your IP address. All of this means that any information that passes between the employee’s computer and your network is secure. It won’t matter if your employee is working from their house or from a café.
System monitoring
Similar to the way remote monitoring can provide a proactive response to threats to WFH systems. Using mobile device management (MDM) or enterprise mobility management (EMM) can make a huge difference in terms of keeping devices safe. They provide enhanced security measures for devices and allow devices to be erased remotely should they be compromised or stolen.
Physical security
Just like with your business, employees need to make sure that they’re taking care of their physical space, as well.
This involves things like making sure you don’t leave computers or company devices in cars or that you don’t leave them at a café table when you go to the bathroom. It also means ensuring that employees don’t use random thumb drives for information. Not only can these be easily lost, but they are very insecure and can contain viruses or malware.
If employees aren’t working out of the house directly, they should also use privacy screens so people around them can’t see what’s happening on the computer.
Education & Training
This one is worth a second mention because it’s important. And because there are security issues that exist in home offices that don’t exist at work. Perhaps the most important thing is to change the default passwords on modems and routers. This isn’t the password you enter to get on your home network, although that shouldn’t be the default password, either. In this case, we’re talking about the router itself. Routers are notoriously bad for having the same default username and password, which is often Admin/Admin. Changing the password isn’t hard, so make sure employees know-how.
You should also include a regular reminder about choosing strong passwords and changing them frequently. It’s easy to forget details like this when you’re working from home. These reminders go a long way.
Separate work and play
As much as possible, provide employees with work-specific computers. This allows you to maintain a controlled system that only has approved apps and programs installed. And, more importantly, it prevents your business from being affected by something that happened off company time.
This is especially relevant because not only are adults working from home, but there are a significant number of students who are doing remote learning as well. Having a separate work computer prevents kids from accidentally doing something that affects your business.

The Cybersecurity FAQ
Does cybersecurity only matter to large companies?
It’s actually the opposite here. SMBs make up the majority of targets for cybercriminals because they often don’t have great protection. The assumption is made that these attacks only happen at major corporations, so SMBs don’t focus on providing adequate protection for their company. Unfortunately, as many as 70% of all small businesses have experienced a cyberattack. What’s worse, of those businesses, 60% never recover.
Does cybersecurity require a large budget?
We get this question a lot. Businesses believe that since IT staff can be expensive and they need to spend a lot of money to get good coverage. But that’s not always the case. You can outsource cybersecurity to a managed security services provider, like Manhattan Tech Support’s security division Kaytuso. You get complete access to a team of cybersecurity experts for a single flat monthly fee.
Can cybersecurity be achieved with a single effort?
It would be great if that were possible, but cybersecurity is a complex issue. Our systems are incredibly dynamic and a single, static solution couldn’t possibly stay on top of everything. The only way to secure such dynamic systems is with proactive maintenance and care. This means thoroughly analyzing your system to identify risks, exposures, and vulnerabilities. Then, you have to use the best tools available to update and tweak your security program as the network environment changes.
Windows Defender is all you need, right?
Sure, Windows Defender has gotten better, but you need more than just a decent antivirus program to keep your business safe. Attacks can come from a number of vectors that even the best antivirus program won’t catch. You need to be sure that every aspect of your business is covered.
Is cybersecurity exclusively an IT problem?
Nope. Not even close. It’s something that everyone, from the CEO down to the team on the loading dock, is responsible for. It’s one of the reasons that education is such a critical part of preventing attacks. The more informed and involved everyone in your company is, the safer your business is, period.
Partner with experts
Of course, one of the best ways to ensure that you’re able to stay on top of cybersecurity in your company is to partner with an award-winning team that is well-versed in security best practices.
Pairing with a team that can manage and monitor your systems remotely can have an enormous impact on preventing attacks, especially one that can provide a robust employee training program and good security practices around passwords.
Doing this can reduce the burden on you and your team. It allows you and your employees to focus on your zones of genius within your business and not get caught up in having to stop and take care of a security threat. When you work with a security partner, you can trust that your systems are secure and up to date.
If you want to learn more about the advantage of partnering with a world-class security team, contact us today.
[sales-phone] | [email-address]



 November 16, 2020
November 16, 2020 Homefield IT
Homefield IT